Cookie-Based Authentication Scenarios
Overview of Scenarios
For example, an organization might have a relatively simple system where, when a user does not have the correct credentials for a content server, the content server redirects the search appliance to a login system for log in, then the login system’s server redirects the search appliance back to the content server after login. This instance is described in Scenario 1: Normal Forms Authentication.
In a different organization, the system might be more complex. For example, the system might require redirecting to one URL to get cookies and then to another URL to get a verified identity. This instance is described in Scenario 3: Cannot Use Universal Login Form and Need Identity Verified Silently.
Each scenario contains detailed information about the interactions between the user, the search appliance, the content server (sample URL, see Sample URL) and login server (redirect URL, see Sample URL Redirect to Login Form) that take place in the different configurations. Read the scenarios so that you can decide which configuration best matches your system’s capabilities and your organization’s requirements.
Cookie-Based Authentication Options
To set up cookie-based authentication, you, as a search appliance administrator, use the following options on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page in Admin Console:
The effects of choosing these options depend on how your system is configured, and whether your system is set up for silent authentication (see Silent Authentication) and cookie cracking (see Cookie Cracking).
|
Scenario 3: Cannot Use Universal Login Form and Need Identity Verified Silently |
|||||
|
Scenario 5: Necessary Cookie is Available for Getting a Verified Identity |
|||||
The following sections provide overviews of each of the options listed in the table.
Sample URL
An example of a sample URL is http://it.abcreports.com/status.html. To detect if a user is logged in, the search appliance sends an HTTP GET message to the sample URL.
If a user is logged in, the sample URL’s content server, it.abcreports.com, returns a 200 response to the search appliance. The 200 response indicates that the request has succeeded. If the user is not logged in, the content server returns a redirect response to the search appliance (see Sample URL Redirect to Login Form).
To specify a sample URL, enter it in the Sample URL box on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page.
Sample URL Redirect to Login Form
If sample URL (see Sample URL) authentication fails, the content server can return a redirect response to the search appliance. The redirect response leads the search appliance to a single sign-on (SSO) system login form.
For example, the sample URL, http://it.abcreports.com/status.html, can redirect the search appliance to an SSO login form at http://abcreports.com/login/login.html. The search appliance can automatically log in to the form by using credentials of the credential group associated with the forms authentication mechanism.
To enable the sample URL to send a redirect response that leads to a login form, check When sample URL fails, expect the sample page to redirect to a form, and log in to that form on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page.
Redirect URL
For example, suppose you specify http://insideabcreports.com/login/login.html as the redirect URL. When authentication at the sample URL fails, the search appliance redirects the user to the SSO login form at http://insideabcreports.com/login/login.html, where it can automatically log in.
If you supply a redirect URL, the authentication mechanism changes significantly. In non-redirect mode, the search appliance transfers a username / password from the Universal Login Form to a login form found when attempting to retrieve the sample URL. With a redirect URL, the search appliance will automatically redirect to that URL. The service at that URL can then authenticate the user in whatever way it wishes. Upon completion of that authentication, the service at the redirect URL should grant a cookie to the user which provides access to secure content (and to the sample URL, if provided), and redirect the user back to the search appliance.
Possible advantages of redirect URL authentication:
Disadvantages of redirect URL authentication:
On balance, Google does not recommend using a redirect URL as a preferred method of authentication.
To specify a redirect URL, enter it in the Redirect URL box on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page.
Return URL Parameter
Silent Authentication
If you require a verified identity, then silent authentication can only be achieved with cookie cracking (see Cookie Cracking).
Cookie Cracking
Your system might require a verified username and/or group, for example to use with authorization by means of policy ACLs, SAML, or connectors. One way of getting a verified username and/or group in addition to silent authentication is to configure the sample URL’s content server for cookie cracking (see Sample URL).
X-Username:value
X-Groups:value1, value2
where value becomes a verified identity for the credential group that is associated with the sample URL.
Using Quoted-Printable Encoding in Response Headers
If special characters are used in an X-Groups or X-Username HTTP response header, the header must be encoded in UTF-8 as quoted-printable. When the search appliance receives the response header, it attempts to decode the UTF-8 quoted-printable encoding.
For example, the search appliance crawls the following content, which contains special characters:
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<meta name="google:aclusers" content="spécial"/>
<meta name="google:aclusers" content="??"/>
<meta name="google:aclgroups" content="spécial-group"/>
</head>
<body>
Some content
</body>
</html>
Because the user "spécial" and group "spécial-group" include special characters, the following encoded headers should be used:
X-Username: sp=C3=A9cial (for spécial)
X-Groups: sp=C3=A9cial-group (for spécial-group)
In contrast, for the user "??" and the group "spécial-group", the following encoded headers should be used:
X-Username: =E6=97=A5=E6=9C=AC (for ??)
X-Groups: sp=C3=A9cial-group (for spécial-group)
If there are special characters in an X-Groups or X-Username HTTP response header that are not encoded, the search appliance is not able to parse the ACL properly. To avoid this problem, Google recommends that you always encode the headers.
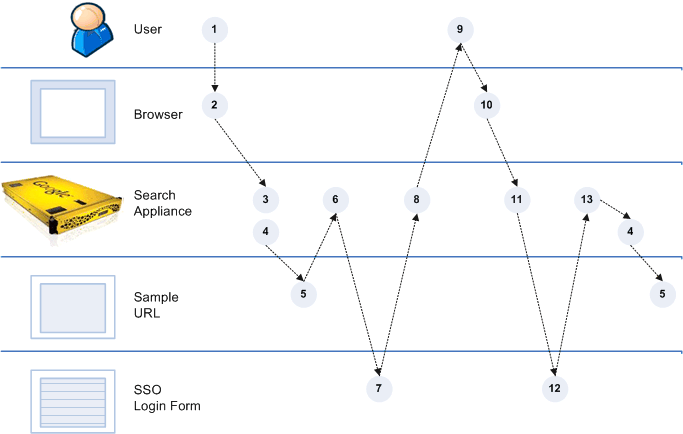
Scenario 1: Normal Forms Authentication
Set Up for Scenario 1
For scenario 1, set up a cookie authentication rule by performing the following tasks:
|
•
|
Specify a Sample URL
|
|
•
|
Check When sample URL fails, expect the sample page to redirect to a form, and log in to that form
|
The redirect to the login form is provided by the sample URL page response, so do not specify it in the Redirect URL box.
Process Overview of Scenario 1
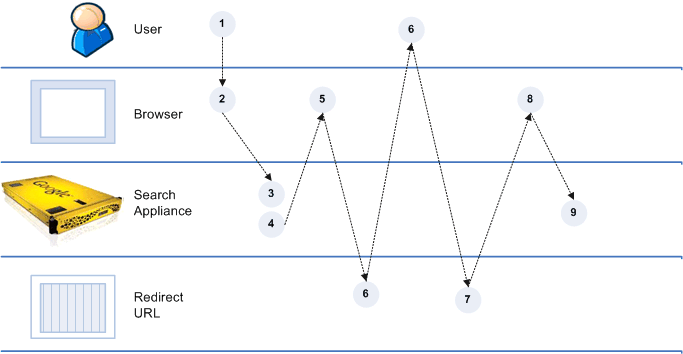
Scenario 2: Cannot Use Universal Login Form
Set Up for Scenario 2
For scenario 2, set up a cookie authentication rule by performing the following tasks:
|
•
|
Specify a Sample URL
|
|
•
|
Specify the SSO Login Form as the Redirect URL
|
Because the sample URL does not redirect to a login form that is compatible with the search appliance, you do not need to check When sample URL fails, expect the sample page to redirect to a form, and log in to that form.
Process Overview of Scenario 2
|
6.
|
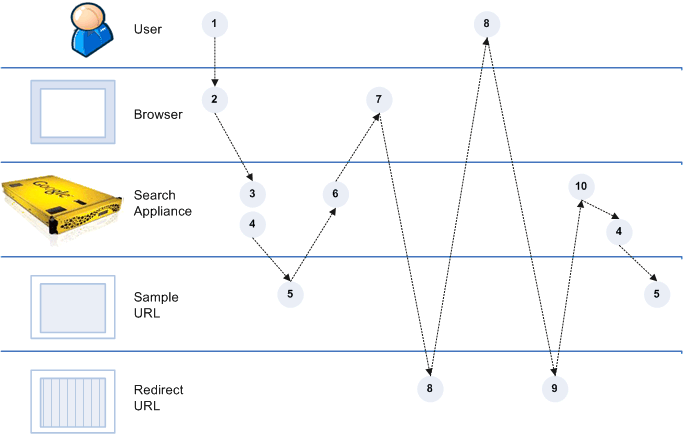
Scenario 3: Cannot Use Universal Login Form and Need Identity Verified Silently
Scenario 3 is a variation of scenario 2 (see Scenario 2: Cannot Use Universal Login Form). As in scenario 2, the system cannot use the Universal Login Form. But in this scenario, you need a verified identity to use with policy ACLs. The sample URL’s server provides the verified identity.
Set Up for Scenario 3
In scenario 3, sample URL’s server is configured for cookie cracking (see Cookie Cracking), meaning that it can provide silent authentication and a verified username and/or groups for the credential group that is associated with the sample URL.
For scenario 3, set up a cookie authentication rule by performing the following tasks:
|
•
|
Specify a Sample URL
|
|
•
|
Specify the SSO Login Form as the Redirect URL
|
Because the sample URL does not redirect to a login form that is compatible with the search appliance, you do not need to check When sample URL fails, expect the sample page to redirect to a form, and log in to that form.
Process Overview of Scenario 3
|
5.
|
If the sample URL check is successful, the content server generates a 200 response that includes a response HTTP header with X-Username:value and/or X-Groups:value and sends it to the search appliance.
|
|
6.
|
Scenario 4: Cannot Provide a Sample URL
Set Up for Scenario 4
For scenario 4, set up a cookie authentication rule by specifying a Redirect URL.
Because your system cannot provide a sample URL, leave the Sample URL box blank and do not check When sample URL fails, expect the sample page to redirect to a form, and log in to that form.
Process Overview of Scenario 4
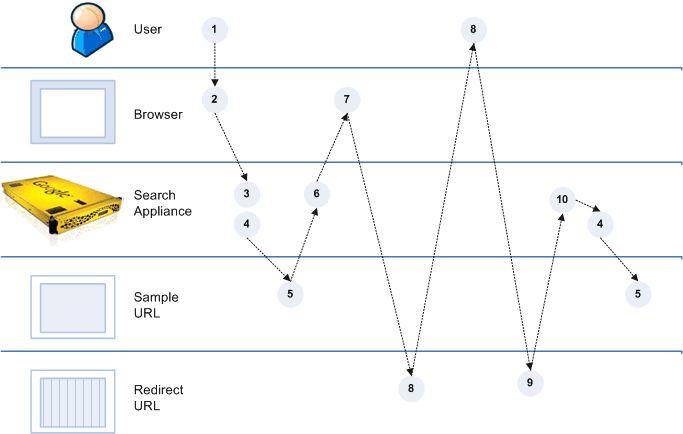
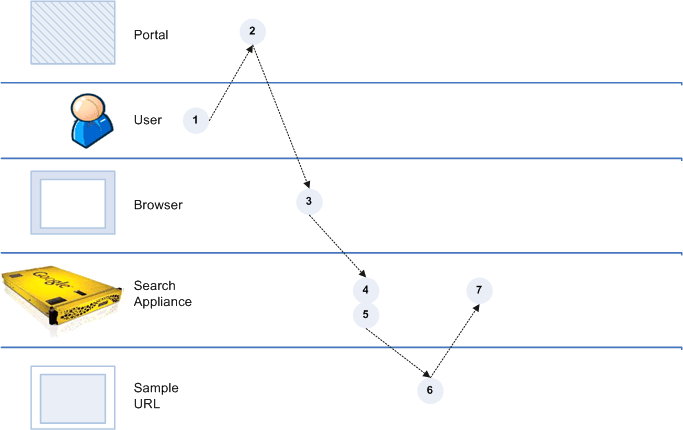
Scenario 5: Necessary Cookie is Available for Getting a Verified Identity
Because the user is already logged in before sending a request to the search appliance, the only way to get a verified identity is by using cookie cracking (see Cookie Cracking).
Set Up for Scenario 5
In scenario 5, the sample URL’s server is configured as a cookie cracker, meaning that it can provide silent authentication and a verified identity for the credential group that is associated with the sample URL. A 200 response from the sample URL includes the X-Username and/or X-Groups HTTP response headers.
For scenario 5, set up a cookie authentication rule by specifying a Sample URL.
Because a cookie is provided to the browser when the user logs into the portal, you do not need to check When sample URL fails, expect the sample page to redirect to a form, and log in to that form or specify a Redirect URL.
Process Overview of Scenario 5
|
6.
|
If the sample URL check is successful, the content server generates a 200 response that includes a response HTTP header with X-Username:value and/or X-Groups:value and sends it to the search appliance.
|
|
7.
|
value becomes a verified identity for the credential group that is associated with the sample URL and authentication is complete.
|
Scenario 6: Use an HTTP Basic Challenge to Get Cookies
Set Up for Scenario 6
For scenario 6, first configure crawl of the content protected by HTTP Basic:
|
1.
|
Open the Content Sources > Web Crawl > Start and Block URLs page and add a URL pattern for the content protected by HTTP Basic and cookies under Start URLs and Follow Patterns.
|
|
2.
|
Click Save.
|
|
3.
|
Open the Content Sources > Web Crawl > Secure Crawl > Forms Authentication page and enter a sample URL for the content protected by HTTP Basic and cookies in the Sample Forms Authentication protected URL box.
|
|
4.
|
Enter a URL pattern in the URL pattern for this rule box.
|
|
5.
|
Click Create. The Admin Console displays an error page, but ignore this error page.
|
|
6.
|
Click Save and Close.
|
|
7.
|
On the Content Sources > Web Crawl > Secure Crawl > Crawler Access page, enter the URL pattern for the content protected by HTTP Basic and cookies under For URLs Matching Pattern, Use.
|
|
9.
|
Click Save.
|
Next, set up a cookie authentication rule on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page:
|
1.
|
Specify a Sample URL.
|
|
2.
|
Check When sample URL fails, expect the sample page to redirect to a form, and log in to that form.
|
The redirect to the HTTP Basic login page is provided by the sample URL page response, so do not specify it in the Redirect URL box.
Process Overview of Scenario 6
The process overview of scenario 6 is the same as the process overview of scenario 1 (see Process Overview of Scenario 1).
Scenario 7: Use an NTLM HTTP Login Page to Get Cookies
Set Up for Scenario 7
For scenario 7, first configure crawl of the content protected by NTLM HTTP and cookies:
|
1.
|
Open the Content Sources > Web Crawl > Start and Block URLs page and add a URL pattern for the content protected by NTLM HTTP and cookies under Start URLs and Follow Patterns.
|
|
2.
|
Click Save.
|
|
3.
|
Open the Content Sources > Web Crawl > Secure Crawl > Forms Authentication page and enter a sample URL for the content protected by NTLM HTTP and cookies in the Sample Forms Authentication protected URL box.
|
|
4.
|
Enter a URL pattern in the URL pattern for this rule box.
|
|
5.
|
Click Create. The Admin Console displays an error page, but ignore this error page.
|
|
6.
|
Click Save and Close.
|
|
7.
|
On the Content Sources > Web Crawl > Secure Crawl > Crawler Access page, enter the URL pattern for the content protected by NTLM HTTP and cookies under For URLs Matching Pattern, Use.
|
|
9.
|
Click Save.
|
Next, set up a cookie authentication rule on the Search > Secure Search > Universal Login Auth Mechanisms > Cookie page:
|
1.
|
Specify a Sample URL.
|
|
2.
|
Specify the NTLM login page as the Redirect URL You do not need to check When sample URL fails, expect the sample page to redirect to a form, and log in to that form.
|
Process Overview of Scenario 7
|
6.
|